Here are two examples from the same phishing campaign. One links to the legitimate Booking.com web site and one links to the legitimate JudicialWatch.org web site. I believe these subdomains normally contain some sort of user profiles, which means the hacker would create or gain control of existing user profiles on these web sites, create the redirector, making them public, then creating the phishing emails linking to them. I could be wrong on how this is done but this is what I believe.
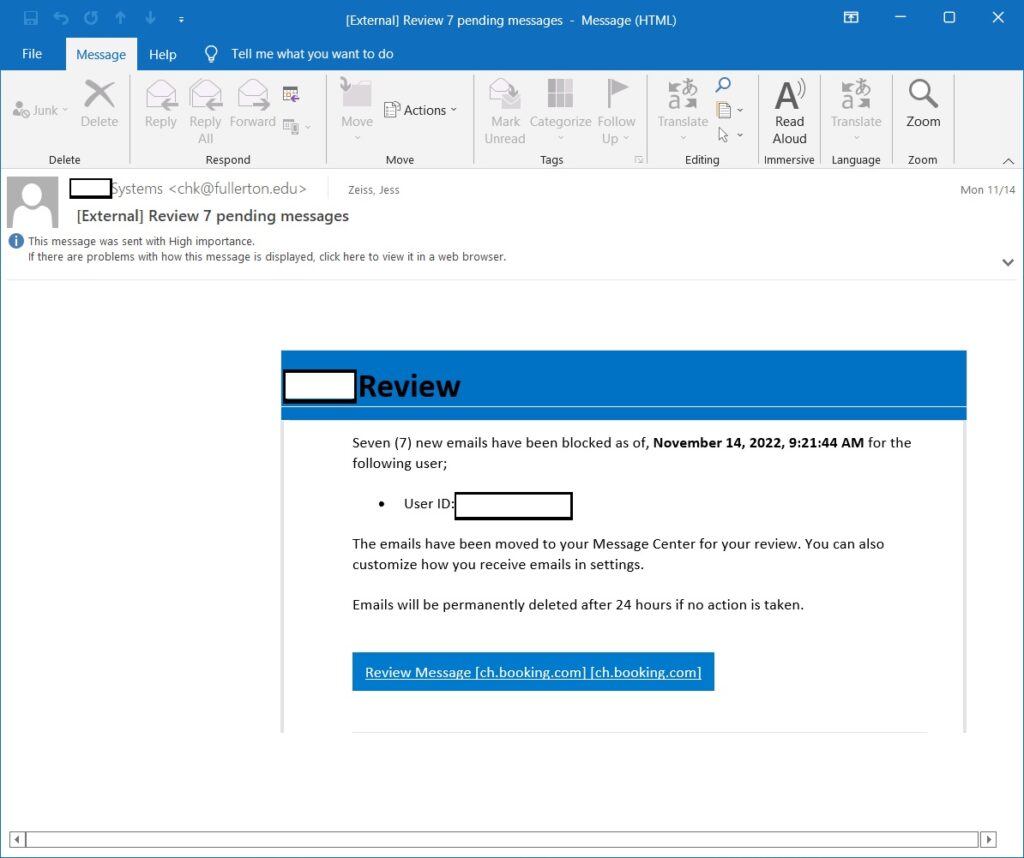
system adds to the rewritten link showing where it actually leads to.
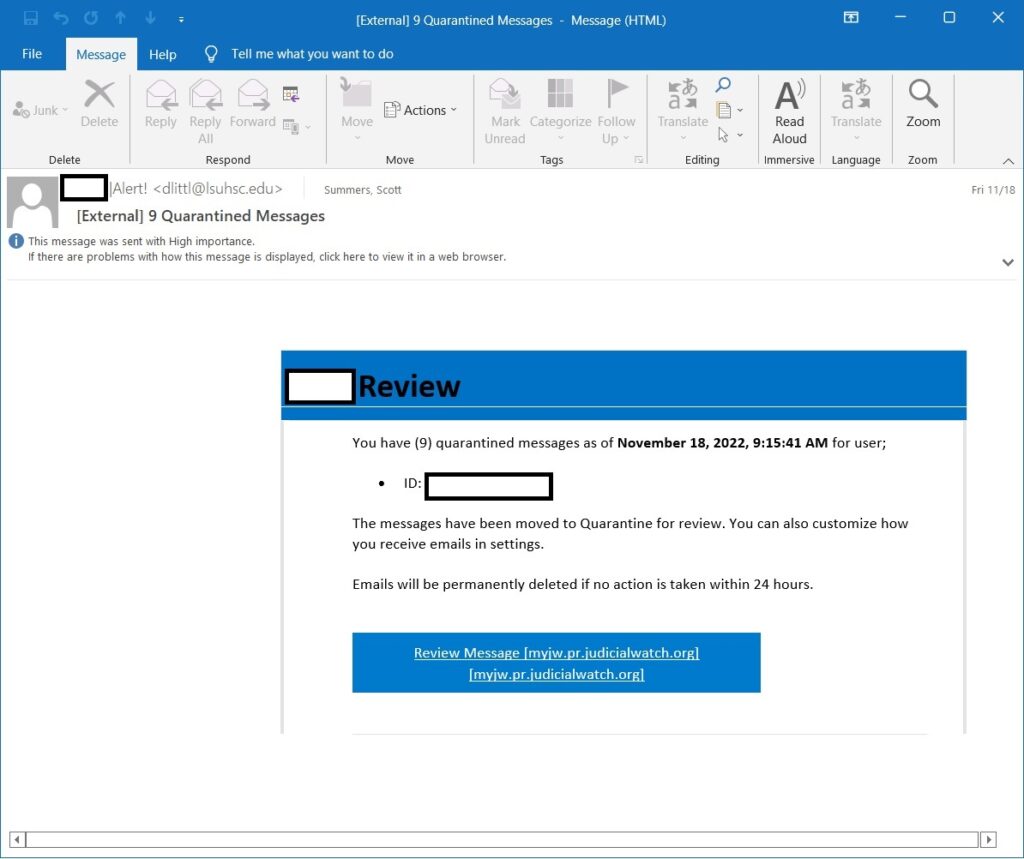
system adds showing where the link leads to. Note the subdomain of myjw.pr.judicialwatch.org.
I would think “myjw” stands for “My JudicialWatch”.
I have informed Judicial Watch of this phishing redirect on their web site. I do not see an option at Booking.com to contact them.
–Matt