No, not this one. But I did find a phish being sent from what appears to be a compromised account linking to a phishing page hosted on a WordPress blog that was either hijacked or else created using the name of the compromised business. The phishing page the email linked to was just one blog post. There is another blog post with a different phish hosted on it.
Here’s the email from the likely compromised email account:
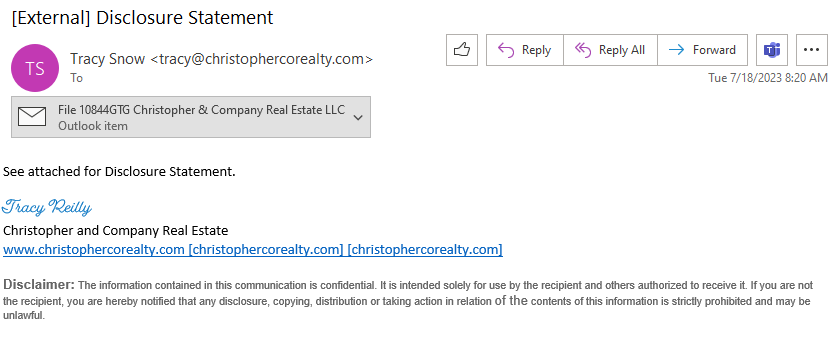
It has another email attached to it. They’re likely doing this because some email security products used to not scan attached .msg files for malicious links or attachments. Does yours? Here is the email that is attached to this one:
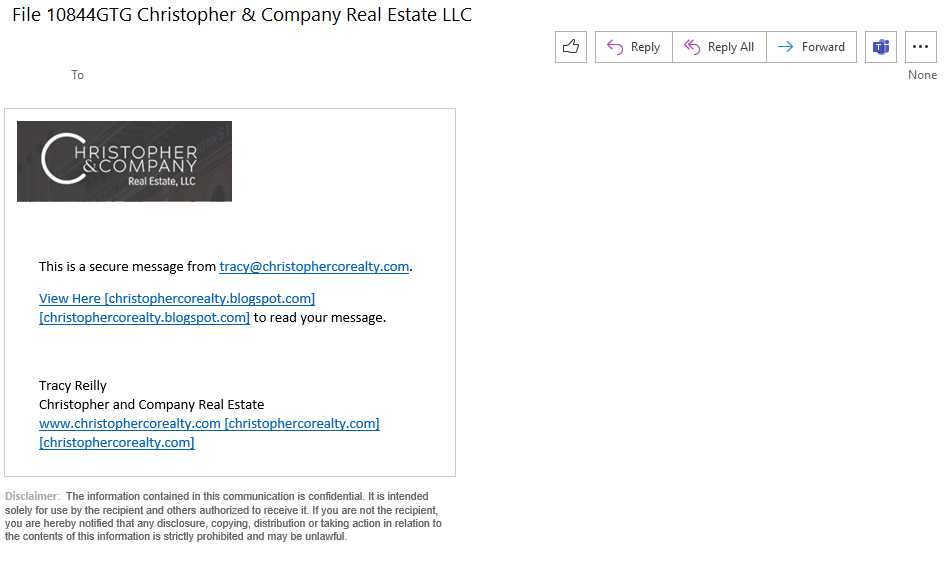
Note the link goes to a Blogspot blog named the same name as the sending domain. Here’s what that page looks like:

This page links to the following page:
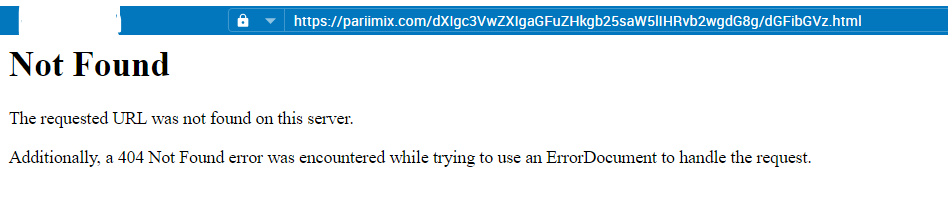
Which, thankfully is no longer available. Going to the root of the Blogspot subdomain, you see a couple of posts including this one, as seen in this screenshot:

Here’s what the other blog post looks like:

This one links to a Google sign-in page that looks to redirect back to the blog as a comment. The blog is likely configured to not post comments immediately, but instead holds them for future publication once approved by the blog owner. Of course in this case, the owner won’t post them. They’ll just hold onto the credentials for future phish or other use of compromised Google credentials.

–Matt