I just came across this phish that had a method of delivering an executable file that I’ve never seen before. The email itself is not that interesting or convincing. Incomplete sentences, typical misspellings, typos and grammatical errors. I suppose it’s vague enough that it might convince someone to click out of curiosity.

Here are the pertinent email headers:

The sending domain does not have a DMARC record so it wasn’t rejected outright. When the link is clicked, it brings up the browser window and downloads a 2MB zip file.
The zip file contains one registry file.
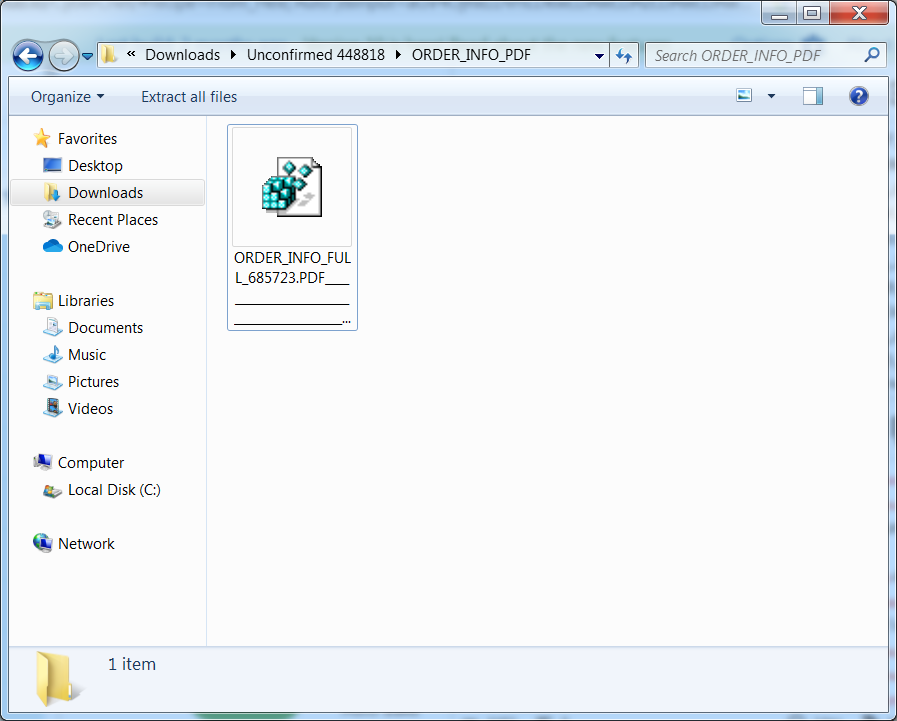
The file name is very long and becomes interesting later.
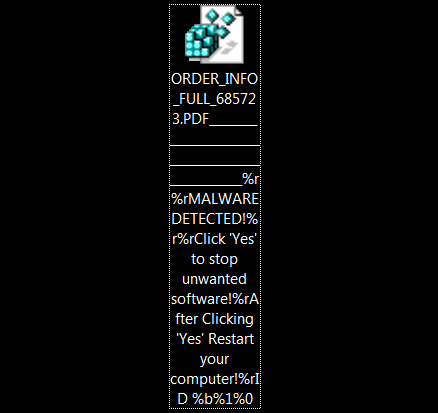
Here are the contents of the registry file. You can see it is obfuscated in hex.

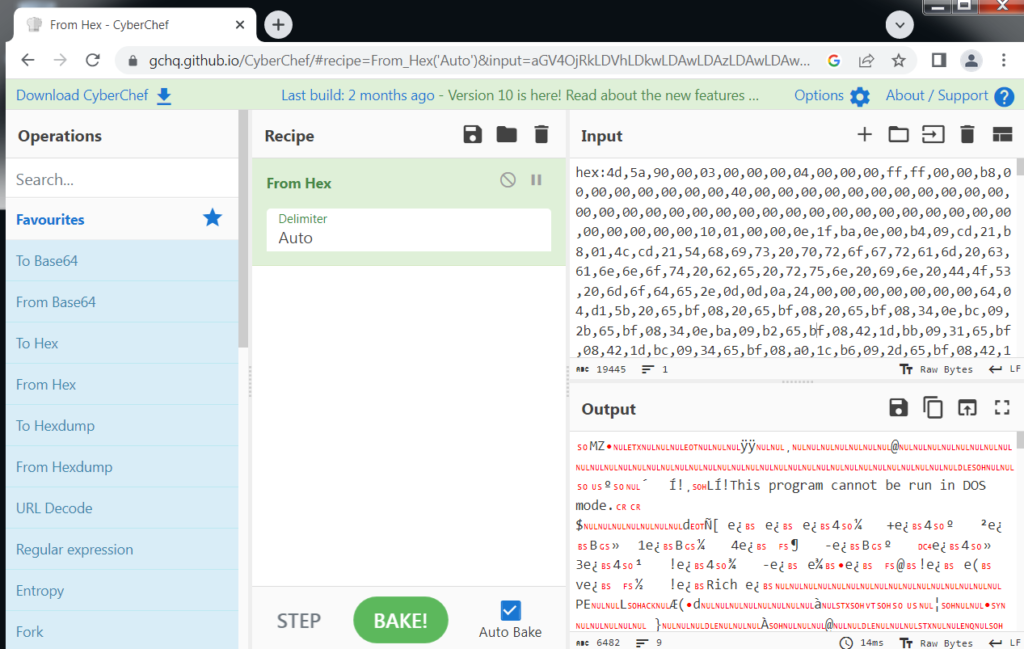
A quick trip through CyberChef and you can see machine code and the typical warning seen in Windows executables.
When you attempt to open it, it attempts to import into the Windows registry, which warns you before importing a file into the registry. Note how the file name is used to try to convince the victim to click Yes to remove all malware from their computer but will actually import the file into the registry. The way I see it, the executable malware is being stored within the Windows registry, which then launches Powershell to decode and execute it.

I imported it into a VM and rebooted. I saw no obvious signs of malware but I’m confident something was running in the background. I’m more interested in malware delivery than what the malware actually does. Maybe I’ll dig into it at a later date.
–Matt
1 thought on “Delivering Executable Using Registry File”